IACD Playbooks and Workflows
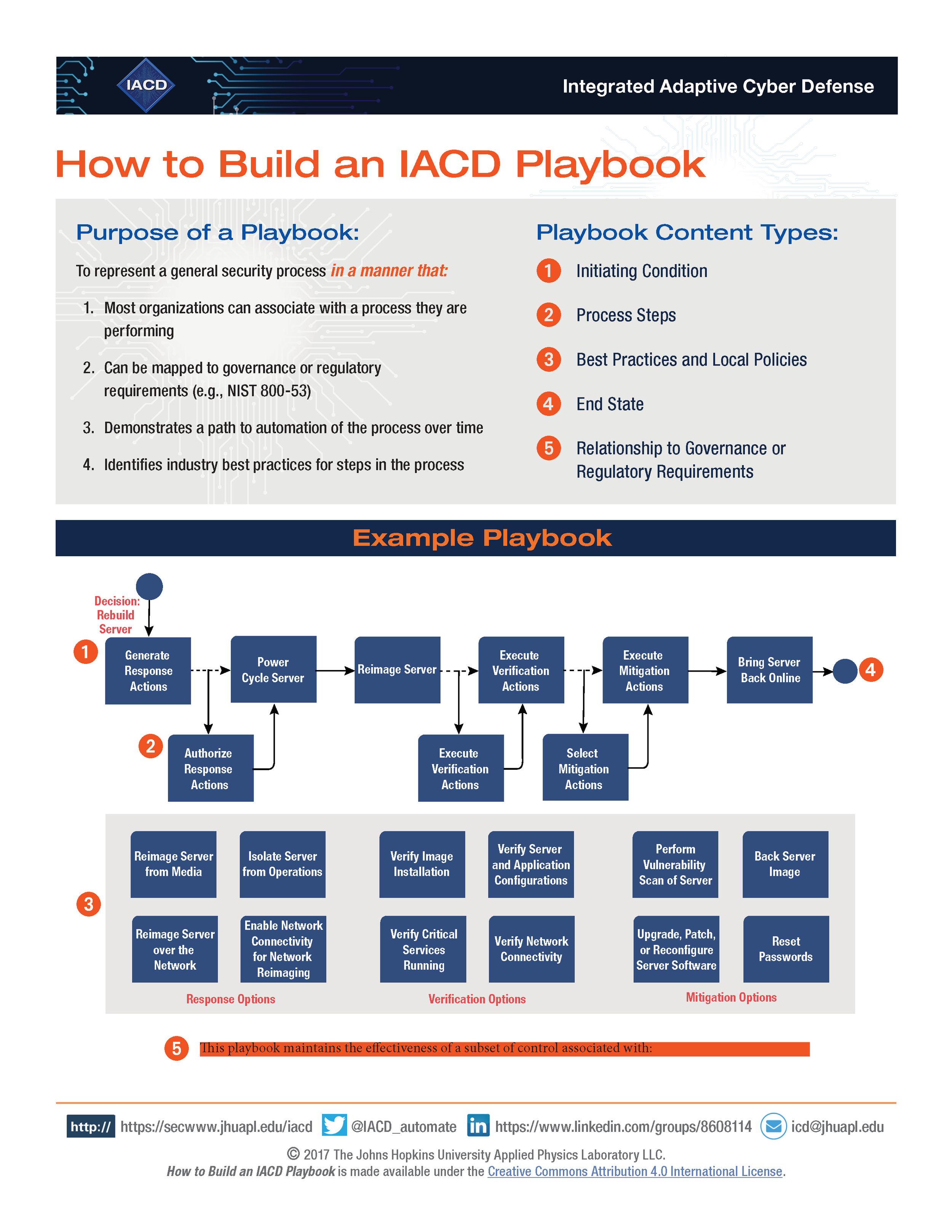
What is a playbook?
IACD provides a mechanism where business- and operations-driven objectives, processes, and controls—including those captured via a Cybersecurity Framework profile—can be translated and applied as automated response actions. Via IACD playbooks, conditions, indicators, and controls that drive the need for cybersecurity responses are captured for orchestration services to monitor and execute.
Playbooks bridge the gap between an organization’s policies and procedures and a security automation and orchestration (SA&O) vendor’s capabilities by showing how an SA&O vendor is able to satisfy a client’s policy and procedure requirements through repeatable and auditable processes, with points where security automation can be implemented.
As you create playbooks for your environment, finding the right content to include and use cases is critical. We provide several references and guides for identifying the best way to achieve these goals as you adopt the IACD framework.
It is important to note that whenever there are options for analysts/operators to select, approve, or authorize, they may choose a “none of the above” option, which simply moves them to the next step in the playbook. For example, in the Compromised Credentials playbook, an organization may not want to take any initial actions to mitigate until they perform more in-depth analysis. Also, a workflow that is implemented at an organization may skip steps depending on conditional logic (e.g., Was the employee fired? If yes, do not do an extra investigation and go straight to restriction of privileges).
What is a workflow?
Workflows are the machine understandable codification of playbooks to enable automation of the procedures. Orchestration services execute workflows, interfacing with the other orchestration services and humans as necessary. Workflows are meant to be machine-to-machine shareable, to include sharing between organizations.
What is a Local Instance?
A local instance is the execution at the System Level. Activity conducted is tailored to a target system. A local instance describes specific decision logic and thresholds and is machine-to-machine sharable in the organization.
For examples of playbooks, workflows, and local instances, see our section on Playbooks, Workflows, & Local Instance Examples.
Playbook THIN SPECIFICATION
To help the creation of IACD playbooks, a specification documents for playbooks is provided here. The purpose of this document is to provide the minimum requirements necessary for current and future Integrated Adaptive Cyber Defense (IACD) participants to create security automation playbooks that are supportive of the IACD framework. This thin specification does not overly prescribe or dictate difficult-to-achieve requirements, but presents the minimum conditions of a well-conceived IACD playbook.